Imagine opening your front door wide and inviting the world to listen in on your most personal conversations. Unthinkable, right? But in the digital world, people inadvertently leave doors ajar, potentially allowing hackers, tech companies, service providers and security agencies to peek into their private communications.
A lot depends on the applications you use and the encryption standards the apps use. End-to-end encryption is a digital security for online interactions. It is used by many of the more popular messaging apps. Understanding end-to-end encryption is critical to maintaining privacy in people’s increasingly digital lives.
While end-to-end encryption effectively protects messages, it is not foolproof against all cyber threats and requires users to actively manage their privacy settings. As a cybersecurity researcher, I believe that continued advances in encryption are necessary to protect private communications as the digital privacy landscape evolves.
How end-to-end encryption works
When you send a message through an app with end-to-end encryption, your app acts as a cryptographer and encrypts your message with a cryptographic key. This process transforms your message into a cipher – a jumble of seemingly random characters that hide the true essence of your message.
This ensures that the message remains a private exchange between you and your recipient, protected from unauthorized access, whether from hackers, service providers or regulatory authorities. If eavesdroppers intercept it, they will only see gibberish and will not be able to decipher the message without the decryption key.
When the message reaches its destination, the recipient’s app uses the corresponding decryption key to unlock the message. This decryption key, stored securely on the recipient’s device, is the only key that can decipher the message and translate the encrypted text back into a readable format.
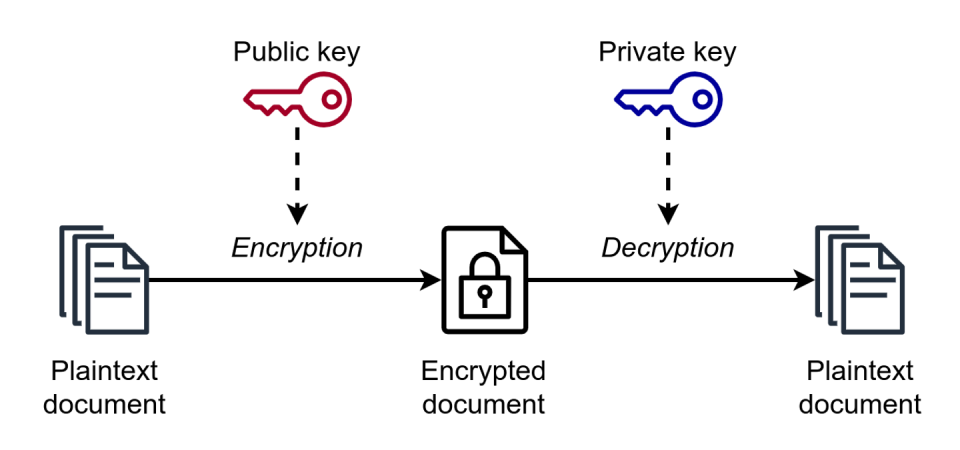
This form of encryption is called public key or asymmetric cryptography. Each party that communicates using this form of encryption has two encryption keys, one public and one private. You share your public key with anyone who wants to communicate with you securely, and they use it to encrypt their messages to you. But that key cannot be used to decrypt their messages. Only your private key, which you don’t share with anyone, can do that.
In practice, you don’t have to think about sharing keys. Messaging apps that use end-to-end encryption do so behind the scenes. You and the party you communicate with securely only need to use the same app.
Who has end-to-end encryption
End-to-end encryption is used by major messaging apps and services to protect user privacy.
Apple’s iMessage integrates end-to-end encryption for messages exchanged between iMessage users, protecting them from outside access. However, messages sent to or received from non-iMessage users, such as text messages to or from Android phones, do not benefit from this level of encryption.
Google has started rolling out end-to-end encryption for Google Messages, the default messaging app on many Android devices. The company aims to modernize traditional text messaging with more advanced features, including better privacy. However, this encryption is currently limited to one-on-one chats.
Facebook Messenger also offers end-to-end encryption, but it is not enabled by default. Users must start a “secret conversation” to encrypt their messages from start to finish. End-to-end encrypted chats are currently only available in the Messenger app on iOS and Android, not on Facebook chat or messenger.com.
WhatsApp stands out for its robust privacy features, implementing end-to-end encryption by default for all forms of communication within the app.
Signal, often heralded by cybersecurity experts as the gold standard for secure communications, offers end-to-end encryption as standard for all its messaging and calling features. Signal’s commitment to privacy is reinforced by its open source protocol, which allows independent experts to verify its security.
Telegram offers a nuanced approach to privacy. Although it offers strong encryption, the default chats do not use end-to-end encryption. To do this, users must start ‘secret chats’.
It is essential to not only understand the privacy features of these platforms, but also manage their settings to ensure the highest level of security that each app offers. With different levels of security for different services, the onus often falls on the user to choose messaging apps wisely and opt for those that offer end-to-end encryption by default.
Is end-to-end encryption effective?
The effectiveness of end-to-end encryption in ensuring privacy is a topic of much debate. Although it significantly improves safety, no system is completely foolproof. Experienced hackers with sufficient resources, especially those supported by security agencies, can sometimes find ways around it.
Additionally, end-to-end encryption does not protect against threats from hacked devices or phishing attacks, which can compromise the security of communications.
The coming era of quantum computing poses a potential risk to end-to-end encryption, as quantum computers could theoretically break current encryption methods, highlighting the need for continued advancements in encryption technology.
Nevertheless, for the average user, end-to-end encryption provides a robust defense against most forms of digital eavesdropping and cyber threats. As you navigate the changing landscape of digital privacy, the question remains: what steps should you take now to ensure the continued protection of your private conversations in an increasingly interconnected world?
This article is republished from The Conversation, an independent nonprofit organization providing facts and trusted analysis to help you understand our complex world. It was written by: Robin Chataut, Quinnipiac University
Read more:
Robin Chataut does not work for, consult with, own shares in, or receive funding from any company or organization that would benefit from this article, and has disclosed no relevant affiliations beyond their academic appointment.